Contact Us:
The Power of Technology
The combination of our expertise and our partner of technology will enable your organizations to better understand, anticipate and shape business outcomes through the ability to minimize the impact of cyber threats.

Protection of a network perimeter including monitoring and filtering the traffic
A few methods of securing a perimeter include NGFW, WAF , IPS, VPNs, and SDWAN
Monitoring and protecting sensitive data to secure privileged credentials
Control and safeguard critical access, ensuring digital fortresses remain impenetrable
Preventing, detecting, assessing, monitoring, and responding to cyber security threats.
SIEM/SOAR provides your organization with advanced detection, response, and analytics for all security events
Protect the endpoint assets as the last touch point of the network it is connected to.
Securing critical accounts & systems, and managing user identities and their resource access.



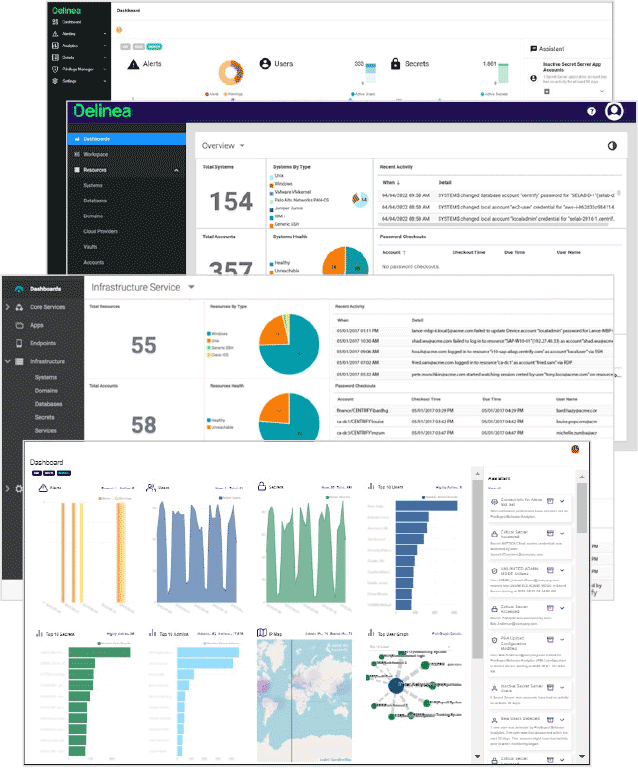
Guard your organization against internal threats and targeted attacks with our Identity and Access Management solutions. Keep your digital assets secure by controlling user access and monitoring for any suspicious activities.
By limiting super-user and administrator privileges (that provide IT Administrators with unfettered access to target systems), least privilege enforcement helps reduce the overall cyber attack surface
Dependable and seamless security to your end users, with single sign-on and lightweight endpoint agents, make applying good security practices frictionless and require minimal intervention
Satisfy Audit and Compliance: Ensure your organization meets regulatory requirements effortlessly with our Identity and Access Management solutions, simplifying audits and compliance checks.